How Do Offshore Software Development Services Bridge the Gaps Existing in Your Business Operations?


The software outsourcing industry is growing in leaps and bounds! The advantages of offshore software development are being leveraged by large-scale as well as small-scale enterprises and even start-ups! Check out some interesting 2022 statistics researched by Zippia.com, about the US outsourcing industry!
- The value of the global software outsourcing market was $92.5 Billion in 2022. This accounted for $62 billion of the entire international market revenue.
- The US outsources approximately thirty-thousand jobs every year.
- 59% of companies outsource to cut costs.
- 66% of the business enterprises in the US outsource services for at least one department.
- 78% of the global organizations that outsource services hold a positive attitude towards their respective technology partners.
- The outsourcing market has been predicted to grow at a CAGR of 4% between the years 2021 and 2025.
Why is software outsourcing so popular? Well, this post discusses how offshore outsourcing models bridge the gap in existing IT operations and why every company, big or small, must consider offshore outsourcing.
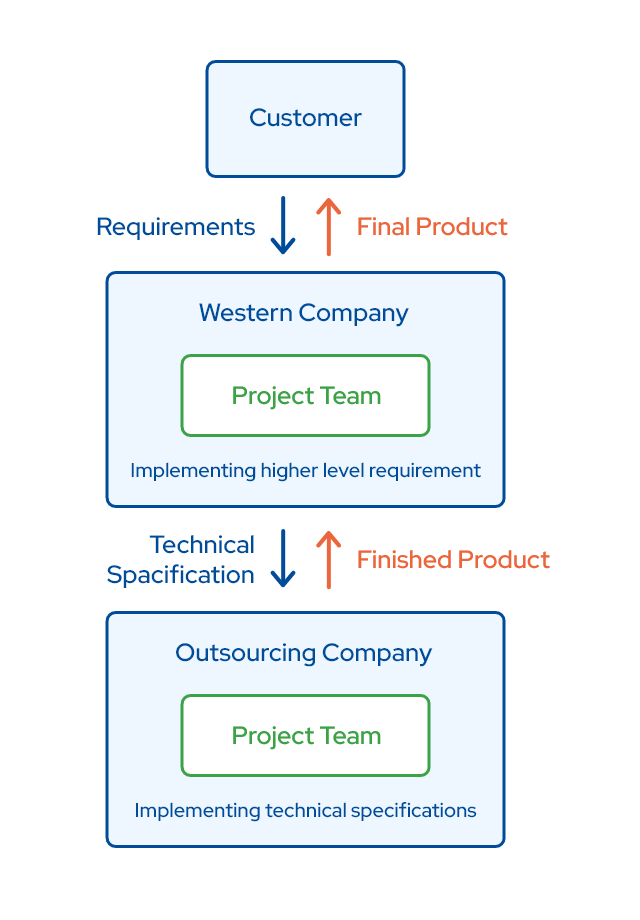
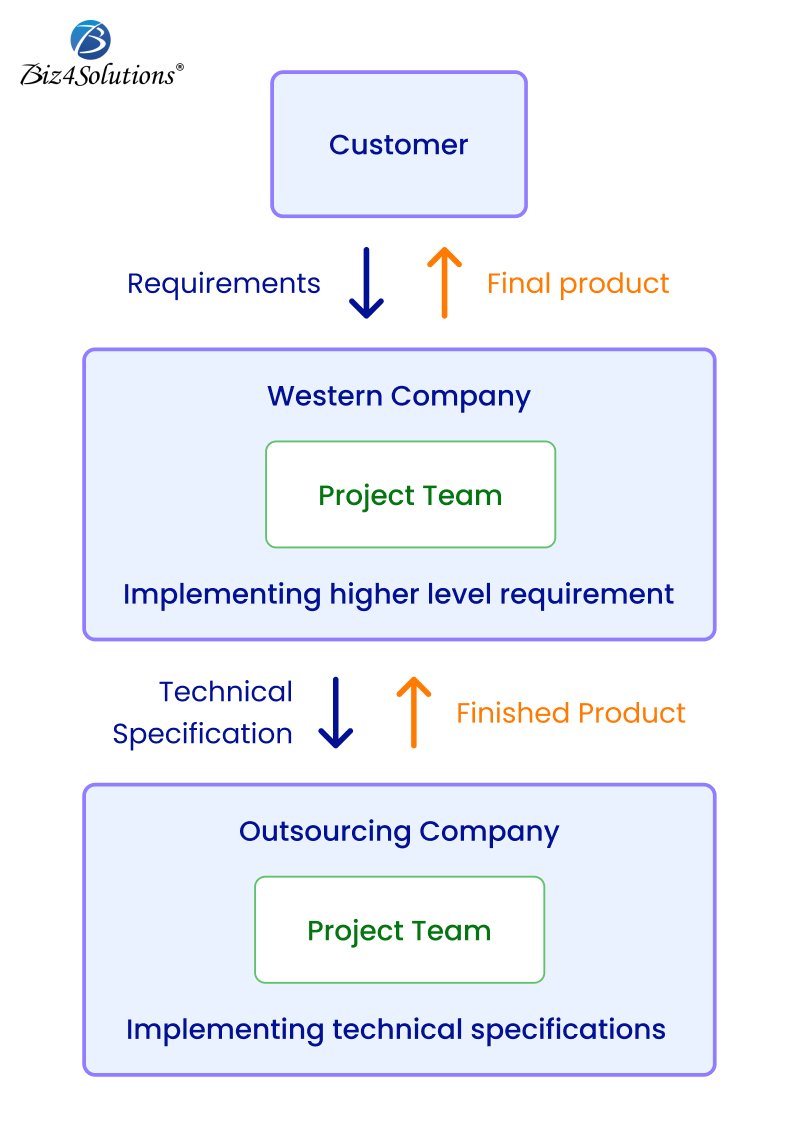
Offshore Outsourcing Software Development Model
Offshore Software Development Services: Long-Term Advantages

Hassle-Free Resource Hiring
For creating an in-house IT team from scratch, you need to invest an enormous amount of time, effort, and money. This is because, for carrying out the processes of recruitment, onboarding, and advanced training to the newly appointed resources; you need to assign resources, working hours as well as funding.
Contrarily, if you adopt the software outsourcing approach, you can save on the cost and hassles of recruitment processes. You just need to define the project requirement and your outsourcing partner will take care of the rest. The offshore firm will provide you with resources that best suit your project specs. The resources can be either dedicated developers or an entire team of software professionals depending on your need.
Usually, software development outsourcing services maintain a curated pool of pre-screened candidates and so, do not need to invest additional time in conducting screening tests, interviews, and coding assessments. As such, your partner company can build a perfect team for you much faster than you can imagine.
Access To Flexible Team Structures
Your business enterprise may not need resources with the same kind of skillsets all the time. A majority of IT projects require a team of professionals with expertise in different areas of IT during various product developmental stages. Moreover, the project requirement may change at any time to keep up with changing times. And, the more flexibility to change the technology stack, team structure, and business model; the faster will the project be able to adapt to ever-evolving specifications.
But, it’s difficult to achieve this flexibility with an in-house team, as it lacks a variety of skillsets. Mostly, you are left with very few options and have to settle down for the available resources even if they do not possess the required years of experience or specialized skills. Several companies invest in training their in-house resources for specific software development tasks.
In this regard, the offshore software development strategy proves beneficial as it offers a flexible team with a wide variety of skillsets for software engineers, programmers, developers, testers, etc. During the initial stages of the product development cycle, when more front-end engineers are needed, your software outsourcing vendor provides you with front-end development experts. And, when the server-side logic is being created, back-end development professionals will be allocated. This approach will be followed with each product development stage. As such, you’ll easily get specialized resources based on the requirement for each developmental phase.
Usage Of the Latest Technologies
Most of the distinguished outsourcing partners have specialists and certified professionals skilled in the latest cutting-edge technologies. Such kind of expertise is rare to find within in-house teams. However, knowledge and expertise to work with emerging tech stacks are necessary for crafting a product that is competitive and relevant as per the modern market requirements.
Addresses Scalability Woes
It’s difficult to identify beforehand how many resources you will be requiring at each stage of your software product development cycle. So, with an in-house development team, scaling up and down as per the project needs become challenging. You either end up overpaying for resources or fall short of resources at certain product development phases.
The offshore software development model helps you to successfully address scaling issues. You can hire extra resources and expand your team when the demand surges or you need to speed up the development process. And, when the demand for resources is low, you may reduce the number of specialists. Offshore partners usually offer various outsourcing models like resource augmentation or dedicated teams, and you get to pick the model that suits you best.
Advantages Of Time-Zone Differences
Remote resources of an offshore development company working from a different time zone may seem challenging to many but is actually a boon for product development. It leads to faster time-to-market. Remote offshore development teams working from different time zones with some overlapping hours make way for continuous services and round-the-clock development activity. And, as there’s always some resource working on the project, you can identify issues at the earliest and resolve them promptly.
This benefit is not available with in-house teams. So, during major service updates, your in-house resources need to work additional hours in late-night shifts. This again involves extra expenses in the form of additional wages to the staff. Contrarily, with the offshore software development approach, you always have IT professionals from different locations working on your project, a few hours ahead or behind your time zone. Hence, changes can be executed without disrupting the normal workflow or asking professionals to work extra hours.
Time To Concentrate on Core Business Functions
Business enterprises that have outsourced development tasks to offshore technology partners do not have to worry about managing complex, time-consuming, and hassle-prone tasks related to project development. This leaves them enough time and energy to focus on core business activities and decision-making processes.
Lower Infrastructure & Operational Costs
The in-house software development approach requires you to invest heavily in infrastructural & operational expenses like maintaining office spaces, employee recruitment, obtaining software licenses, paying salaries to IT professionals, employee supervision, and many more. Also, you need to spend a humongous amount to keep your IT ecosystem relevant and updated with the latest market trends.
Hence, outsourcing software development to third-party companies saves you from all hassles as you only need to pay for the services delivered by a dedicated development team or developers for the project assignment within a said timeline. However, the labor costs in some countries like the US, Australia, Canada, etc. are very high regardless of the experience and expertise of the workforce. On the other hand, outsourcing software development services in India will enable you to get a skilled workforce at minimal costs. Such an offshore business model promises to offer a partnership with experienced tech nerds, affordable product development rates, and flexible pricing models to choose from.
It has been observed so far that offshore software development services outsourced from South Asian countries like India offer the maximum value for your money.
Advanced Tools Used by Offshore Companies to Bridge the Communication Gap with Clients
It is essential for your in-house team to have continual and seamless communication with offshore software development teams. For this reason, most experienced outsourcing partners have a well-built communication infrastructure. It allows continuous, prompt, transparent, and secure communication with clients regardless of time-zone differences. Advanced tools such as Zoom, Slack, Skype, Hangout, Asana, LastPass, HelloSign, Hackpad, etc. are used for convenient and safe communication between both parties. For instance, Slack, Google Hangout, and Skype are utilized for offering regular updates, Jira for project updates, Hubstaff for managing time, GitHub for managing the code, and so on.
An experienced offshore software development company has been using these advanced communication tools for years and so, the team members are well-trained in their usage. Such tools allow the client to effortlessly track the performance of their offshore team members, handle reporting functions, and understand the status of the project at any given time. Team calls via video conferencing are one of the most popular practices for synching the members of teams working from different locations.
Are You Interested in Building a Top-Class Website or Mobile App?
Wrapping Up:
The offshore software development model brings a lot to the table for business enterprises. It offers benefits like access to a large pool of talent, innovation, and expertise. Offshoring also promises a cost-efficient development cycle. Besides, you can get much-needed advice and new business insights from your experienced software outsourcing company, leading to productive outcomes and flawless decision-making.
You need to just select the right offshore team with the necessary experience and expertise needed for your project.